Administrator
Handbook
www.loriotpro.com
Administrator
Handbook |
TOC |
FCAPS Standardization
Introduction
LoriotPro is a management and supervision solution that follows the International Telecomunications Union. The ITU defined the TMN architecture (Telecomunication Management Network) in 1988.
However this model is oriented to Telecomunication and Network and LoriotPro is more than a Network Manager but should be seen as a Information System Supervisor and Manager. Devices supervised by Loriotpro include systems and servers, network devices, printers, industrial peripherals etc..
The TMN has five layers slipting the enterprise operations:
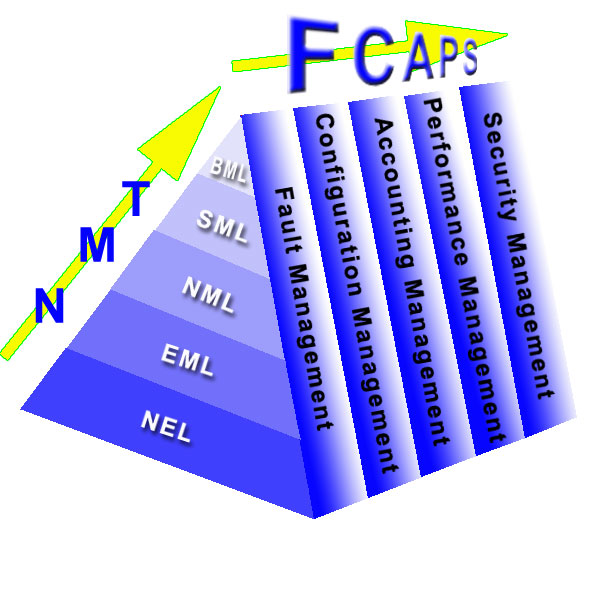
BML - Business Management Layer
Manage the overall business, acheiving return on investment, market share, employee
satisfaction, community and governmental goal.
SML - Service Management Layer
Manage the service offered to customer or internal users, meeting customer service
level, service quality, cost and time-to-market objectives
NML - Network Management Layer
Manage the network and systems that deliver those services, capacity, diversity,
and congestion
EML - Element Management Layer
Mange the elements comprising the networks and systems
NEL - Network Element Layer
Switches, routers, tramission, distribution systems
All these layers have to be manage for being operationnal
and performant. That is where the FCAPS concept is introduced.
In an effort to provide focus and consistency in the area of Network Management,
the International Organization for Standardization (ISO) developed an international
network management model known as the FCAPS model. This model identifies five
key areas that make up the backbone of network management:
Fault Management
Configuration Management
Accounting Management
Performance Management
Security Management
To give you a better idea of how LORIOTPRO can help you to manage your Information System we used this model and try to identify how good or bad :-) our products answer to the FACPS requirements. These appreciations and notations are totally non objective because we assign them but we tried to be as honest as possible. Remember that you can test our product and figure out by yourself the truth and the lie.
Fault
Management
Fault Management is a set of functions which enables
the detection, isolation and correction of abnormal operation of the telecommunication
network and its environment. Fault management ensures that service remains available.
Fault Detection
Fault Correction
Fault Isolation
Network Recovery
Alarm Handling
Alarm Filtering
AlarmGeneration
Clear Correlation
#
| Note | LoriotPro Achieving |
|---|---|
# is the first goal of LoriotPro. the huge number of health indicator to supervise in an Information System is impossible without a centralize solution that collect and display those indicators. LoriotPro provides first a convenient way of vitually storing the devices to manage. They are classified in a directory tree structure that is fully designed by the administrator thus the structure is always well adapted to the company infrastructure or organization. Visual current status of devices are displayed in almost real time in the directory but alos on graphical IP Map (the InternetWork MAP) or in organisationnal view (Active View). The # with LoriotPro is very fast because the faulty device or application is pinpointed by its color in a blink of an eye. Additionnal programs called Plug-in provided other ways for #. Among these one : Process Surveyor detect faulty or missing processus under Windows or Unix, Bulk Trheshold Control detects any changes or incorrect values in the SNMP MIB objects, Bulk TCP poller detects unresponding TCP ports etc... |
Abstract from : ITU-T Recommendation
M.3400
Fault Correction transfers data concerning the repair of a fault and for the
control of procedures that use redundant resources to replace equipment or facilities
that have failed.
Fault Correction includes the following function sets:
• Management of repair process function set.
• Arrangement of repair with customer function set.
• Scheduling and dispatch administration of repair forces function set.
| Note | LoriotPro Achieving |
|---|---|
Fault Correction in the Information System
is not directly performed by LoriotPro. LoriotPro helps the administrator
to fast identified a failed node within the infrastructure. Generally
the failed node and/or is failed application are managed by proprietary
configuration tools. One useful capability of LoriotPro is to start the
configuration tools when the device is selected (A telnet session, a WEB
access ...). Anyway, when the default is hardware a human intervention
is necessary.
|
| Note | LoriotPro Achieving |
|---|---|
The localization of the fault is obvious with the MAP display (the responsible equipment is red colored) and with the Healt Control Center that filters devices by its location in the directory and by its current status. Furthermore, for huge networks with hundreds of nodes a search tool help to find a device in the directory or on the MAP. Actions can be taken on status change and start a diagnostique tool dedicated to the incriminated device. The verification of connectivity is available everywhere in the GUI by simple ping or SNMP request or with advanced diagnostique tools like our graphical TraceRoute or the Path Trace tool. To find faults in Switch and Bridge network achitecture using the spanning Tree algorithm us the Spanning Tree Bridge MAP plug-in. |
| Note | LoriotPro Achieving |
|---|---|
The localization of the fault is obvious with the MAP display (the responsible equipment is red colored) and with the Healt Control Center that filters devices by its location in the directory and by its current status. Furthermore, for huge networks with hundreds of nodes a search tool help to find a device in the directory or on the MAP. Actions can be taken on status change and start a diagnostique tool dedicated to the incriminated device. The verification of connectivity is available everywhere in the GUI by simple ping or SNMP request or with advanced diagnostique tools like our graphical TraceRoute or the Path Trace tool. |
Alarm Handling
Definition:
Abstract from : ITU-T Recommendation M.3400
A TMN provides the capability to monitor NE failures in near-real time. When
such a failure occurs, an indication is made available by the NE. Based on this,
a TMN determines the nature and severity of the fault. For example, it may determine
the effect of the fault on the services supported by the faulty equipment. This
can be accomplished in either of two ways: a database within a TMN may serve
to interpret binary alarm indications from the NE, or if the NE has sufficient
intelligence, it may transmit self-explanatory messages to a TMN. The first
method requires little of the NE beyond a basic self-monitoring capability.
The second method requires additionally that both the NE and a TMN support some
type of message syntax that will allow adequate description of fault conditions.
Alarm information can be reported at the time of occurrence, and/or logged for
future access. An alarm may also cause further management actions within the
NE that lead to the generation of other fault management data.
In order to enable the TMN to perform alarm surveillance, NEs must:
• Allow monitoring of alarm conditions in a near-real time or scheduled
manner.
• Allow querying of alarm conditions existing on the NE.
• Allow logging and retrieval of historical alarm information.
Alarm Surveillance includes the following function sets:
• Alarm policy function set.
• Network fault event analysis, including correlation and filtering function
set.
• Alarm status modification function set.
• Alarm reporting function set.
• Alarm summary function set.
• Alarm event criteria function set.
• Alarm indication management function set.
• Log control function set.
• Alarm correlation and filtering function set.
• Failure event detection and reporting function set.
| Note | LoriotPro Achieving |
|---|---|
The Event Manager from LoriotPro provides the monitoring of the events (alarm condition and informationnal status) occuring in the network, on the systems and application. Events are the result of traps (SNMP alarm sent by the devices or the application) or event directly created by LoriotPro on a SNMP polling result. By reading the objet value of any SNMP aware device and by setting threshold on these values and/or status, LoriotPro triggers alarm (event) generation. Event are immediatly displayed in the Event Monitor and store in log file for futher analysis.
|
Definition: See Alarm Handling
| Note | LoriotPro Achieving |
|---|---|
The Event Manager from LoriotPro includes
a powerfull
filter engine that allows filtering on muliple criteria. The configuration
is either perfomed directly in a config file of from an advanced wizard
graphical interface. Filters are available for LoriotPro Events or SNMP
traps. The Syslog Collector product provides the same advanced filtering
capabilities for the SYSLOG
messages standard. The filtered message could triger actions (SMTP
message, trap forwarding, syslog forwarding, execution of programs).
|
Definition: See Alarm Handling.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro is able to generate events (alarm) on SNMP value threshold and on non reponding polling. LoriotPro integrates a powerfull polling engine that is able to poll hundreds of hosts either with ping or SNMP requests. Failed pollings triggers alarms of various severity. This polling engine is fully configurable, polling interval, type of polling, set of SNMP oid, maintenance period...Plug-in are also able to generate alarm on conditions, Process Surveyor detect faulty or missing processus under Windows or Unix and generates, Bulk Trheshold Control detects any changes or incorrect values in the SNMP MIB objects, Bulk TCP poller detects unresponding TCP ports etc...
|
Clear
Correlation
Clear Correlation is used for clearing alarms that are
the result of an initial event. Clearing the source event of subsequent alarm
should clear all the correlated alarms.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro is not able to do Alarm Clear correlation. Alarm clearing is realized one by one or by group but not with correlation. However, the Event Browser is a LoriotPro Plug-in dedicated to the retrieval of historical alarm information. This powerful Log files browser and search engine could scan all your log file history for finding the event predefined by key words. Intuitive correlation could be done by the administrator at this level.
|
Configuration
Management
Configuration Management provides functions to exercise control over, identify,
collect data from and provide data to NEs.
Resource Utilisation
Network Provisioning
Auto and Sub rack Discovery
Backup and Restore DataBase Handling
Resource Shutdown
Change Management
Support For Preprovisionning
Inventory Asset Management
Resource Utilisation
Ressource utilisation in an information system is controled by collecting usage statistics on each device that provide services.This data can be used to determine whether the service product is appropriately matched to the user needs. It can be used to forecast demand before a loss in quality of service.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provide the control of resource utilisation by graphically displaying on line grahics or counters graphics the current and past usage rate. The variety of counter provided in the MIB files allows a fine control of who is using what. Tools that are able to control ressource utilization with LoriotPro are the Interface Monitor, the various linear and counter Graphics, the MRTG graph, the LoriotPro style Graph.
|
Abstract from : ITU-T Recommendation M.3400
Network Planning and Engineering deals with the functions associated with determining
the need for growth in capacity and the introduction of new technologies. It
involves evaluation of alternate plans and the entry of chosen plans into a
database that will support the Provisioning function group. Once a plan has
been specified, the Provisioning function group will fill in further designed
parameters and proceed toward implementation of the plan.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro do not provide tools for defining provisioning plan but provides trend analysis with long term information that helps the administrator to perform provisionning. With such information it is easier to provision a ressource upgrade before the overload. The setting of threshold on usage levels allows the triggering of events and informs the administrator that upgrades are necessary.The Bulk Trheshold Control Plug-in detects any changes or incorrect values in the SNMP MIB objects and helps to provision resources on reached trheshold. |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provides advanced discovery tools. The Discover process is a state of the art discovery module that is able to find by multiple ways the presence of any IP device. The starting point for a discover could be the LoriotPro platform or a remote (router) node. The scope of the discover is fully configurable in term of Hops, SNMP version ... Other tools helps the discover process to build a clear image of the Information System, the IP/SNMP scanner, the Trace Route and Internetwork Path, Netbios Name Resolver. |
Backup and Restore Database Handling
| Note | LoriotPro Achieving |
|---|---|
Feature not provided by LoriotPor |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro is one of the best tools on the market for Ressource Shutdown detection. The core of the program is an advanced polling process which scan the availaibility of hundreds of hosts in few minutes. |
| Note | LoriotPro Achieving |
|---|---|
Change management is not the goal of the product
from the point of view of human ressources training. The discover
process only help the administrator to detect any change (new system
or device added or removed) by performing full intelligent scanning of
the network. |
| Note | LoriotPro Achieving |
|---|---|
LoriotPor provide trend analysis with long term information that helps the administrator to perform provisionning. The setting of threshold on usage levels allows the triggering of events and informs the administrator that upgrades are necessary. |
Inventory management support involves maintaining a record of all the Network Element resources that are installed in an Information system, form network devices to software applications.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro with its integrated concept of Directory provides by default inventory management. The location, the quantities of equipment, their model numbers, serial numbers, software and hardware versions, installation dates can be collected and diplayed immediatly in dialog box or in WEB report. Furthermore, custom values can be attached to each device and categorize hosts on proprietary values. An integrated search engine finds any of these ressources in few seconds. An enhanced WEB scripting language performing background SNMP requests allows the administrator to built up to date reports on the current asset. Additionnal Plug-in dedicated to Cisco devices collect and save the current version of IOS. Discovery process, the IP/SNMP scanner and the Trace Route tools performs advanced search for discovering any non registered devices. |
Accounting Management enables the measurement of the use of network services and the determination of costs to the service provider and charges to the customer for such use. It also supports the determination of prices for services.
Track service ressource
usage
Cost for services
Accounting Limit
Combine costs for multiple
resources
Set quotas for usage
Audits
Toll fraud reporting
Support for different modes
of accounting
Track service/ressource
usage
Abstract from : ITU-T Recommendation M.3400
An OS within the TMN can collect data from NEs which is used to determine charges
to customer accounts. This type of function may need extremely efficient and
redundant data transport capabilities in order to maintain records of billing
activity. Often the processing must be carried out in near real time for a large
number of customers.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provides trend analysis with long term information that helps the administrator to perform provisionning. The setting of threshold on usage levels allows the triggering of events and informs the administrator that upgrades are necessary. |
Cost for services
Abstract from : ITU-T Recommendation M.3400
A tariff is a set of data within a NE that is centralized within an Intelligent
Network or distributed into the exchanges, or in an Operations System, used
for the determination of the amount of payment for services used. A tariff may
include dependency on the tariff class, which is defined according to service,
origination and destination, and on the tariff period and day class.
| Note | LoriotPro Achieving |
|---|---|
Only one Plug-in from LoriotPro is directly connected to cost management. The Cisco ISDN statistics provided detailed information on Calls duration and thus can be used to calculate cost. |
Set limits on the usage of resources, for example disk space, network bandwith, login period ...
| Note | LoriotPro Achieving |
|---|---|
The Accounting limit management is possible
with LoriotPro but limited to the SNMP SET command options available
on the device.
|
Combine costs for multiple resources
| Note | LoriotPro Achieving |
|---|---|
Not provided |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro is able to perform setting on any device and on any settable SNMP object. If disk space can be limited from SNMP LoriotPro provides the SET command that control the usage. SET can be performed directly in some MIB table like available in intergated tools like the Common Query tool. It is also possible to set limits (threshold) that will trigger an alarm when this limit is reached. |
| Note | LoriotPro Achieving |
|---|---|
Schedule audits and reports could be realized with LoriotPro. An internal scheduler can perform report generation. Reports are scripts that are executed on demand. Scripts can contain all the information available by SNMP or contained in the Directory. It is for example possible to print all the routing table of routers within a network in a single report, to collect the list of installed application on system ... |
| LORIOTPRO | Response |
Not provided |
Support for different modes of accounting
| LORIOTPRO | Response |
Not provided |
Performance Management
Performance management involves the periodic collection
of quality of service metrics QOS that characterize the performance of the network
and system resource. One of its goal is to to find network congestion and bottlenecks
and minimized them by subsequent action.
Utilisation and error rates
Consistent performance level
Performance Data Collection
Performance report generation
Performance Data Analysis
Problem reporting
Capacity Planning
Performance data/statistics
collection
| Note | LoriotPro Achieving |
|---|---|
LoriotPro is the ideal tool for finding errors and setting alarm thresholds on tolerable values. The SNMP MIB contains by default tons of indicators on error rates and exploiting them with LoriotPro is a matter of few mouse clicks. Additionnal programs called Plug-in provided other ways for #. Among these one : Process Surveyor detect faulty or missing processus under Windows or Unix, Bulk Trheshold Control detects any changes or incorrect values in the SNMP MIB objects, Bulk TCP poller detects unresponding TCP ports etc... |
| Note | LoriotPro Achieving |
|---|---|
The first level of performance that LoriotPro collect is the availibility. By polling at regular interval all the hosts located in your IS, LoriotPro provides you with an in depth view on the availibility of your ressources. By default line graph and counter graphs shows the availibity and performance of your hosts. This proactive monitoring preemts any degradation in service quality. |
Performance
Data Collection
Involves the periodic collection of quality metrics that
characterize the performance of the network resources over service intervals.
It also facilitates the visualization of trends that can indicate periodic or
gradual degradation of physical resources.
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provides the internal process for gathering data statistics over service intervals. Internal timers trigger hundred of SNMP polling requests toward the Network Elements and retreive data statistics used for real time statistics or trend analysis. |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provides trend analysis with long term information that helps the administrator to make performance analysis. WEB Report with line graph are generated from this collected data |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provides trend analysis with long term information that helps the administrator to make performance analysis. The TraceRoute Plug-in for example provides detailed values on round trip time with mininmum, maximum and average values. |
| Note | LoriotPro Achieving |
|---|---|
Problem reporting is possible with an integrated E-mail system that forward events and alarms to predefined E-mail address. Event log could be printed and use as reports either for all hosts or on a host by host basis. |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro provide trend analysis with long term information that helps the administrator to perform provisionning. The setting of threshold on usage levels allows the triggering of events and informs the administrator that upgrades are necessary. |
Performance data/statistics collection
| Note | LoriotPro Achieving |
|---|---|
Statistics are available on availibilty and
perfomance for each host located in the directory and polled at
regular interval. |
Security Management should minimize unauthorized or
accidental access to network control functions. Security management functions
deals with ensuring legitimate use, maintening cinfidentialities, data integrity
and auditability.
Abstract from : ITU-T Recommendation M.3400
Security Management provides for the management of security. In addition, security
of management is required for all Management Functional Areas and for all TMN
transactions. Security of management appears as part of the Security Function
in ITU-T M.3010.
Selective resource
access
Enable NE functions
Access logs
Security Alarm/Event reporting
Data Privacy
User access rights checking
Security breaches and attempts
Security audit trail log
Selective resource
access
| Note | LoriotPro Achieving |
|---|---|
LoriotPri support SNMP v3 that allows a selective access to agent indicators and data. The LoriotPro WEB console intergates user access control and provides a fine tuning of what objects can be seen in the directory tree. |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro does not provide solution for enabling NE functions except device SNMP v3 configuration |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro and the Syslog Collector solution
provide a perfomant solution for Syslog message management. Syslog messages
are use to log security information in many Unix based Firewal and proprietary
one like PIX from Cisco. The Syslog solution is able to filter severe
security alarms among a high flow of log. |
Security Alarm/Event reporting
| Note | LoriotPro Achieving |
|---|---|
LoriotPro and its advanced Event management is able to manage security alarms either comming from Syslog collector agent or SNMP devices. SNMP Alarms (events) are either result of SNMP polling results or received traps. |
| Note | LoriotPro Achieving |
|---|---|
LoriotPro does not provide solution for data privacy. LoriotPro includes mechanisms that guarantee data privacy of its own protocol. |
| Note | LoriotPro Achieving |
|---|---|
The LoriotPro WEB console intergates user access control and provides a fine tuning of what objects can be seen in the directory tree. This feature allows the delegation of partial management work. |
Security breaches and attempts
| Note | LoriotPro Achieving |
|---|---|
THe bulk threshold Plug-in is a good tool for testing security breach in Firewall for the TCP open ports. IP/SNMP scanner helps the administrator to detects SNMP aware hosts and those that are opened to attacks with common communities. |
| Note | LoriotPro Achieving |
|---|---|
Audit trail are are also maintain in the common log. All access could be log as LoriotPro events. |
 www.loriotpro.com
www.loriotpro.com |
|